Your Account
Personal profile and security preference configuration
Account
Account Configuration Architecture
Account settings centralize personal profile information, security preferences, and connected service integrations within the TelemetryOS administration interface. Understanding these configuration options enables selection of appropriate defaults aligned with organizational security policies and operational requirements.
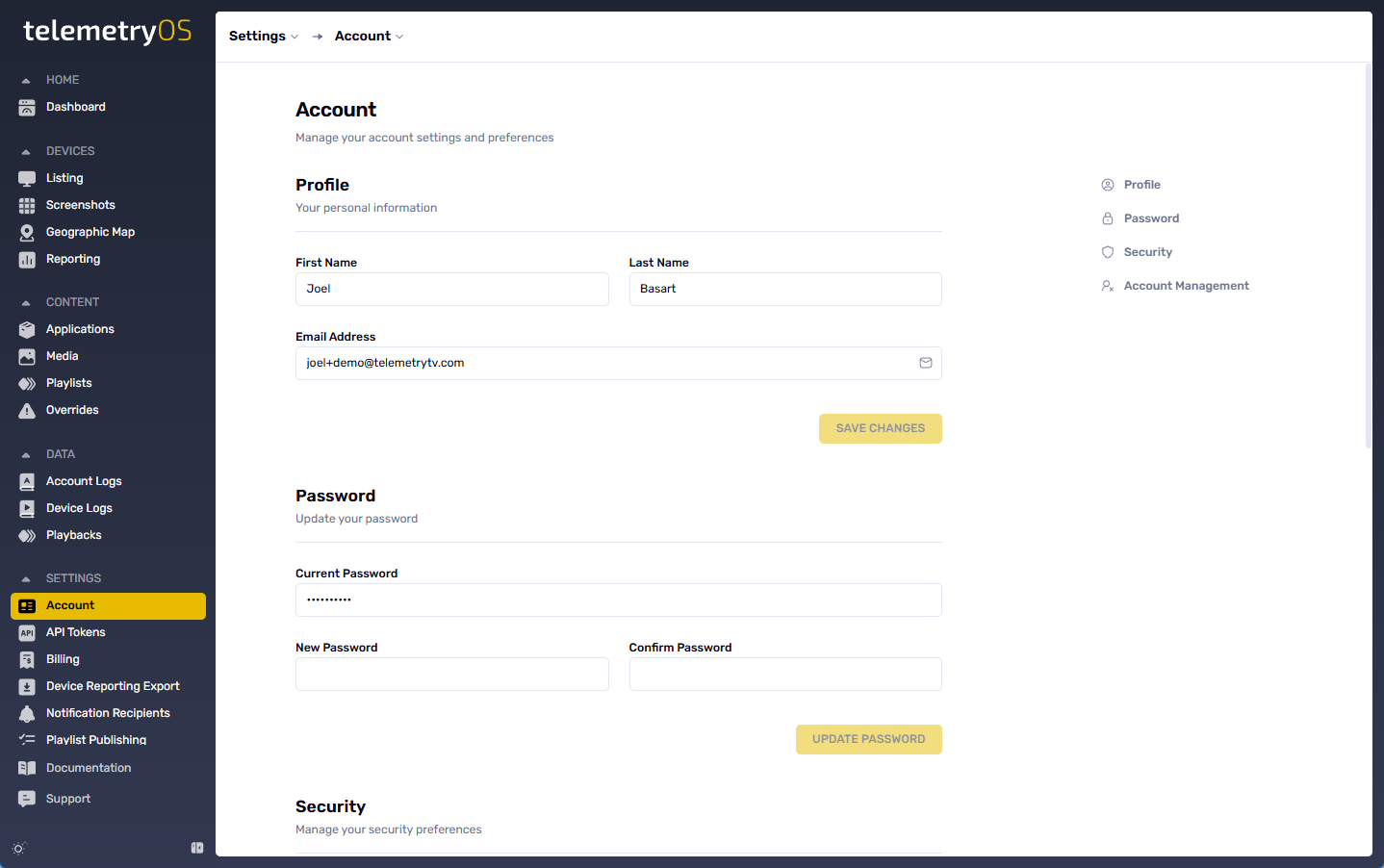
Profile
Profile information includes name, email, and time zone settings. Current profile data ensures accurate notification delivery and timestamp representation aligned with working hours. Email changes typically require verification to maintain account security and prevent unauthorized access. Time zone configuration affects schedule display and log timestamp rendering throughout the administration interface.
Security
Security settings control sign-in and session protection. Passkeys provide passwordless, phishing‑resistant access using device biometrics or security keys. Password usage pairs with multi‑factor authentication (MFA) to add a second factor such as an authenticator app. Secure recovery code storage enables access recovery if devices are lost. Session controls support active session review, access revocation from other devices, and session lifetime alignment with organizational risk profiles.
Connected services
External identity provider linking like Google or GitHub enables OAuth‑based sign‑in, or organizations may enforce SSO through identity providers. Connected services support revocation at any time when changing tools or when integrations no longer meet policy requirements.
Recommendations
A few defaults work well for most users:
| Area | Recommendation | Why |
|---|---|---|
| Sign‑in | Prefer passkeys where supported | Strong, phishing‑resistant authentication |
| Passwords | Use long, unique passwords + MFA | Reduces takeover risk when passkeys aren’t available |
| Recovery | Keep two passkey authenticators or secure backup codes | Prevents lockout after device loss |
| Sessions | Periodically sign out of unused sessions | Limits exposure if a device is misplaced |
Account actions
Account ownership and deletion policies vary by organization. In general, disabling access is preferable to deletion because it preserves audit history while removing login capability. Where deletion is required by policy, ensure you have exported any necessary data and that ownership of shared assets is transferred to another administrator before proceeding.
Related topics
Updated 26 days ago