User Management
Multi-user account architecture and role-based access control
TelemetryOS supports multi-user account structures where multiple individuals access shared organizational resources with role-based permissions. This collaborative architecture enables teams to manage digital signage deployments without sharing credentials, maintaining individual accountability and granular access control.
User Capacity Architecture
Account plans include user capacity limits that define the maximum number of user accounts that can access organizational resources. These limits vary by subscription tier, with higher-tier plans supporting larger teams and more complex organizational hierarchies.
User capacity constraints protect account security and ensure fair resource allocation across subscription tiers. When user limits are reached, account expansion requires subscription tier adjustment or direct coordination with TelemetryOS Support for enterprise deployments. Reseller-managed accounts coordinate capacity adjustments through reseller partners who maintain billing relationships.
User Creation Methods
TelemetryOS supports three distinct user creation workflows, each suited to different organizational needs and authentication requirements:
Email invitation enables self-service password setup where invited users receive email prompts to establish their own credentials. This method maintains security by ensuring passwords never transit through administrator accounts and supports standard email verification workflows.
Manual credential creation provides administrator-controlled account provisioning where credentials are established directly without self-service workflows. This approach suits scenarios requiring immediate account access or environments where invited users may lack reliable email access during onboarding.
Team Login (Enterprise plans) enables bulk user provisioning with Single Sign-On integration, supporting large-scale team onboarding through identity provider integration rather than individual account creation.
Email Invitation Workflow
Email invitation workflows separate credential establishment from account creation, enabling users to set their own passwords without administrator involvement. This self-service approach maintains password confidentiality and reduces administrative overhead for user onboarding.
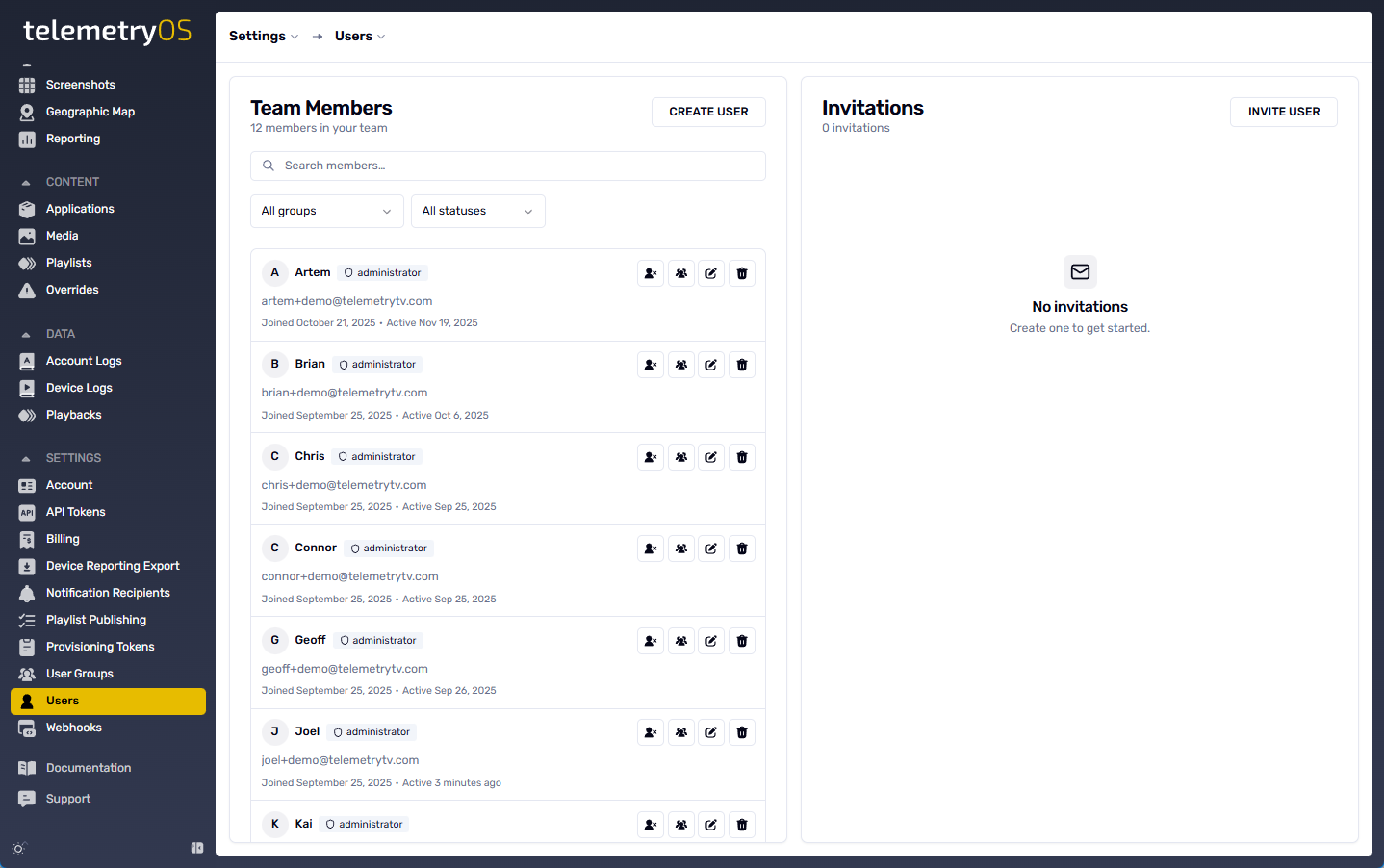
Invitation workflows require email address specification and user group assignment during account creation. Group assignment determines permission scope and resource visibility—administrators can constrain access to specific device organizations, content types, or system features through group-based permissions.
Email invitations contain time-limited activation links that prompt password establishment and account verification. Unactivated invitations expire after a defined period, requiring re-invitation if users fail to complete setup within the activation window.
Detailed invitation workflows and troubleshooting procedures are documented in User Invites.
Manual Credential Provisioning
Manual credential provisioning enables administrator-controlled password establishment, bypassing self-service invitation workflows. This approach suits scenarios requiring immediate account access or environments where email-based workflows introduce unacceptable delays.
Manual provisioning requires complete user profile establishment including email address, name information, initial password, and group assignments. Administrators bear responsibility for communicating credentials securely to users through out-of-band channels, as passwords established through manual provisioning never transmit via email.
This workflow proves valuable for emergency account provisioning, service accounts requiring programmatic access, or organizational contexts where email reliability constraints make invitation workflows impractical.
User Lifecycle Management
User accounts support ongoing management throughout their lifecycle, including profile updates, permission modifications, and activity monitoring.
Profile Management
User profiles contain identity information (name, email address) and permission associations (group memberships). Profile updates enable administrators to correct contact information, adjust permissions by modifying group assignments, or update identity data when organizational changes occur.
Email address updates affect authentication—users must authenticate using their current email address even if profile updates are pending. Group membership changes take effect immediately, with affected users experiencing updated permission scopes upon their next account interaction.
Password Management
Administrator-initiated password resets provide account recovery capability when users lose access credentials or when security incidents require credential rotation. Password reset operations establish new credentials without requiring user participation, enabling account recovery for users lacking email access or experiencing authentication failures.
Reset workflows generate new passwords that administrators communicate securely to affected users. Users should change administrator-assigned passwords after regaining account access, following standard security practices.
Activity Monitoring
User accounts maintain activity logs that provide visibility into authentication patterns and account usage. Activity data includes authentication timestamps, source IP addresses, authentication methods (password, SSO, API token), and account creation metadata.
This audit data supports security investigations, helps identify inactive accounts suitable for deactivation, and provides compliance evidence for access control requirements. Authentication method tracking enables administrators to identify accounts requiring migration to updated authentication mechanisms when security policies evolve.
Updated 2 months ago